
A recently uncovered security vulnerability named “Sinkclose” has been found to affect a wide range of AMD processors, including both EPYC and Ryzen chips. This news has raised concerns about the security of millions of computers worldwide that use these popular CPUs.
The Sinkclose Vulnerability…?
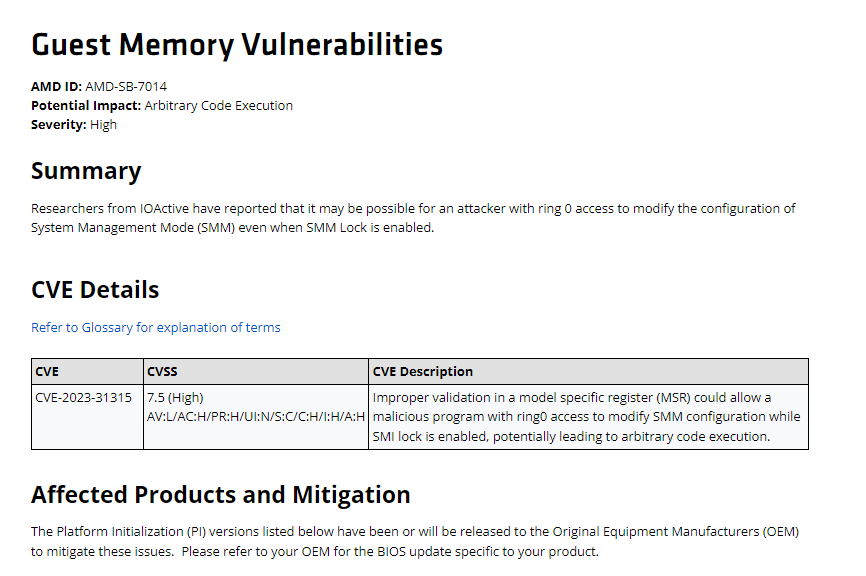
The Sinkclose vulnerability targets a crucial component of AMD’s Ryzen and EPYC processors, potentially allowing unauthorized access to sensitive data and code insertion. This security flaw has reportedly been present in AMD CPUs for over a decade, highlighting the long-standing nature of the issue.
Researchers from the security firm IOActive brought this vulnerability to light at the recent Defcon hacker conference. The flaw enables intruders to execute malicious code when the CPU is in “System Management Mode,” a sensitive state that manages critical firmware operations.
To exploit this vulnerability, attackers would need deep access to an AMD-based computer or server. They could potentially use a type of malware called a bootkit, which is particularly concerning because it can evade detection by antivirus software.
AMD’s Response and Mitigation Efforts
AMD has acknowledged the Sinkclose vulnerability and expressed gratitude to the researchers for bringing it to their attention. In response, the company has taken several steps to address the issue:
- Released a security bulletin detailing the vulnerability
- Published a comprehensive list of affected processors, including Ryzen 3000 and newer, as well as 1st Gen EPYC and later server CPUs
- Developed firmware and microcode patches to mitigate the vulnerability across various CPU generations
It’s worth noting that while AMD has identified the core issue, there’s still work to be done in terms of fully mitigating the vulnerability. This will likely involve a BIOS update for affected systems.
What This Means for Users
For the average consumer, there’s no immediate cause for alarm. However, it’s crucial to stay informed and take appropriate action when updates become available. Users of affected AMD processors should keep an eye out for BIOS updates from their device manufacturers or motherboard vendors.
To address the vulnerability in its most severe form, users would need to physically open their computer and use a hardware-based programming tool called an SPI Flash programmer. This process is complex and not recommended for the average user.
As we wait for more comprehensive solutions, it’s essential to maintain good cybersecurity practices, such as keeping your system updated, using reputable antivirus software, and being cautious about downloading files or clicking on links from unknown sources.
While the discovery of the Sinkclose vulnerability is concerning, it’s a reminder of the ongoing challenges in maintaining cybersecurity in our increasingly connected world. As AMD works on resolving this issue, users can take comfort in knowing that the company is actively addressing the problem and providing solutions to protect their systems.




