Security researchers discovered an updated version of FakeCall malware targeting Android users through sophisticated call hijacking techniques. This banking trojan now intercepts calls made to financial institutions, redirecting them to cybercriminals instead of legitimate bank representatives.
Banking Trojan’s Enhanced Capabilities
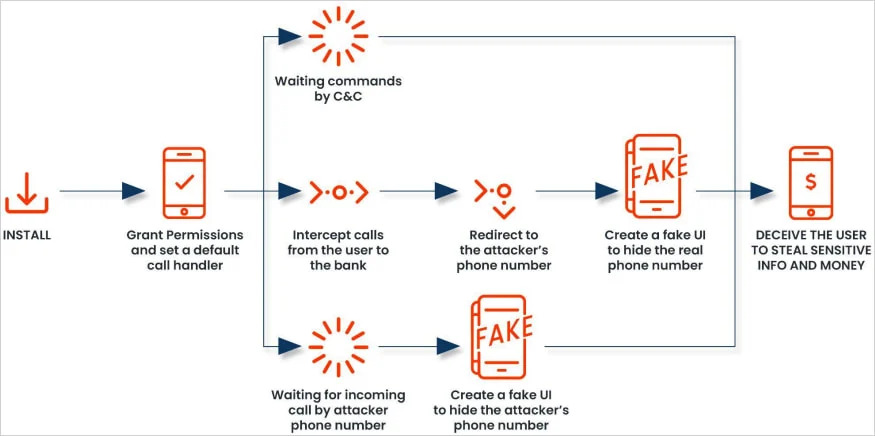
The malware operates by requesting permission to become the default call handler on infected Android devices. Once granted this access, it creates a convincing replica of the standard Android dialer interface, complete with authentic-looking contact information. When users attempt to contact their bank, the malware secretly redirects the call to scammers while displaying the genuine bank phone number on screen.
This deceptive approach builds upon previous versions of FakeCall, which focused on voice phishing schemes. The earlier variants prompted users to initiate calls through malicious apps impersonating financial institutions. The latest iteration eliminates this step by directly intercepting regular outgoing calls.
Technical Advancements and New Features
Security firm Zimperium uncovered several technical improvements in the malware’s latest version. The developers implemented stronger code obfuscation techniques to avoid detection while expanding its functionality through Android’s Accessibility Service. This grants the malware extensive control over the device interface, enabling automated permission requests and simulated user interactions.
The updated version includes new capabilities controlled through a command-and-control server. These features allow attackers to:
- Track device location
- Remove applications
- Capture audio and video recordings
- Edit contact information
- Stream device screen content
- Take screenshots
- Unlock devices temporarily
- Manipulate home button functions
- Access and upload photos from storage
The malware specifically targets the DCIM folder, which typically contains user photos and media files. It can compress and transmit these files to remote servers controlled by attackers.
Security experts noted the malware maintains an active development cycle, suggesting regular updates and improvements from its creators. While researchers published technical indicators to identify infected apps, cybercriminals frequently modify these identifiers to bypass detection.
Users should exercise caution when installing Android applications, particularly those distributed through APK files outside the Google Play Store. Though malicious apps occasionally bypass Google Play’s security measures, Google Play Protect can remove them upon detection.
The emergence of FakeCall demonstrates cybercriminals’ increasing sophistication in targeting mobile banking users. By combining call interception, convincing user interface replicas, and extensive device control capabilities, this malware represents a serious threat to Android users’ financial security.
This banking trojan’s evolution from basic voice phishing to automated call hijacking highlights the importance of maintaining device security and being cautious when granting permissions to applications. The malware’s ability to capture sensitive data while remaining undetected makes it particularly dangerous for users who regularly conduct banking activities on their mobile devices.
Security researchers are closely watching FakeCall’s growth and looking for new versions. With its added features and better hiding tactics, the malware’s creators seem set on targeting more banks and users globally.
Read this also: Game Freak’s Pokémon Secrets Leaked in Major Data Breach





